When we think of online crime, we normally divide it into two neat categories. Hackers are the techies in hoodies who crack into databases. Scammers are the fast-talkers who send fake emails or make calls. But in today’s world, that line has blurred. More often than not, hackers and scammers work together — and that’s bad news for ordinary people.
The logic is simple: hackers steal the raw material (your data), while scammers turn it into money (your trust, your panic, your payments). Let’s unpack why this partnership exists, how it works, and what it means for you.
Table of Contents
Hackers: The Data Suppliers
Hackers are like burglars. Their skill is breaking into vaults of information: emails, passwords, phone numbers, even medical and financial records. These attacks are called data breaches when criminals break in, or data leaks when companies accidentally expose your details.
But after a big breach or leak, hackers don’t usually want to waste time targeting individuals one by one. That’s inefficient.
Scammers step in here. They don’t need technical skills. What they need is a convincing story. And if hackers provide your personal details, their story instantly sounds more believable.
Example: In 2020, attackers breached Twitter’s internal tools, hijacked accounts of Elon Musk, Barack Obama, and others, and launched a Bitcoin scam. Hackers broke in, scammers cashed out.
What this means for you: You may never “get hacked” yourself, but if a company you use is compromised, that stolen data can quickly resurface in a scam email or call targeting you.
From Anonymous Breaches to Personal Scams
When headlines announce “500 million records stolen,” it sounds abstract. But those big, faceless breaches quickly become personal.
- Equifax (2017): Hackers stole Social Security numbers of 147 million Americans. Scammers used them to file fake loans and tax returns.
- Facebook (2021): 533 million users’ phone numbers leaked after a database was left unprotected. Soon after, people worldwide reported scam texts that included their real names (Wired).
- LinkedIn (2021): Data of 700 million users appeared for sale. Scammers posed as recruiters, using real job titles and company names to trick victims (CNBC).
What this means for you: That scam text or phishing email feels personal because it is — scammers are pulling your details straight from old hacks or leaks.
The Dark Web: The Criminal Marketplace
Why do hackers and scammers need each other? Because of the underground marketplace where stolen data gets traded: the dark web.
Hackers rarely scam people themselves. Instead, they sell data in bulk to minimize risk. Scammers, who specialize in manipulation, buy this data cheap and flip it for profit.
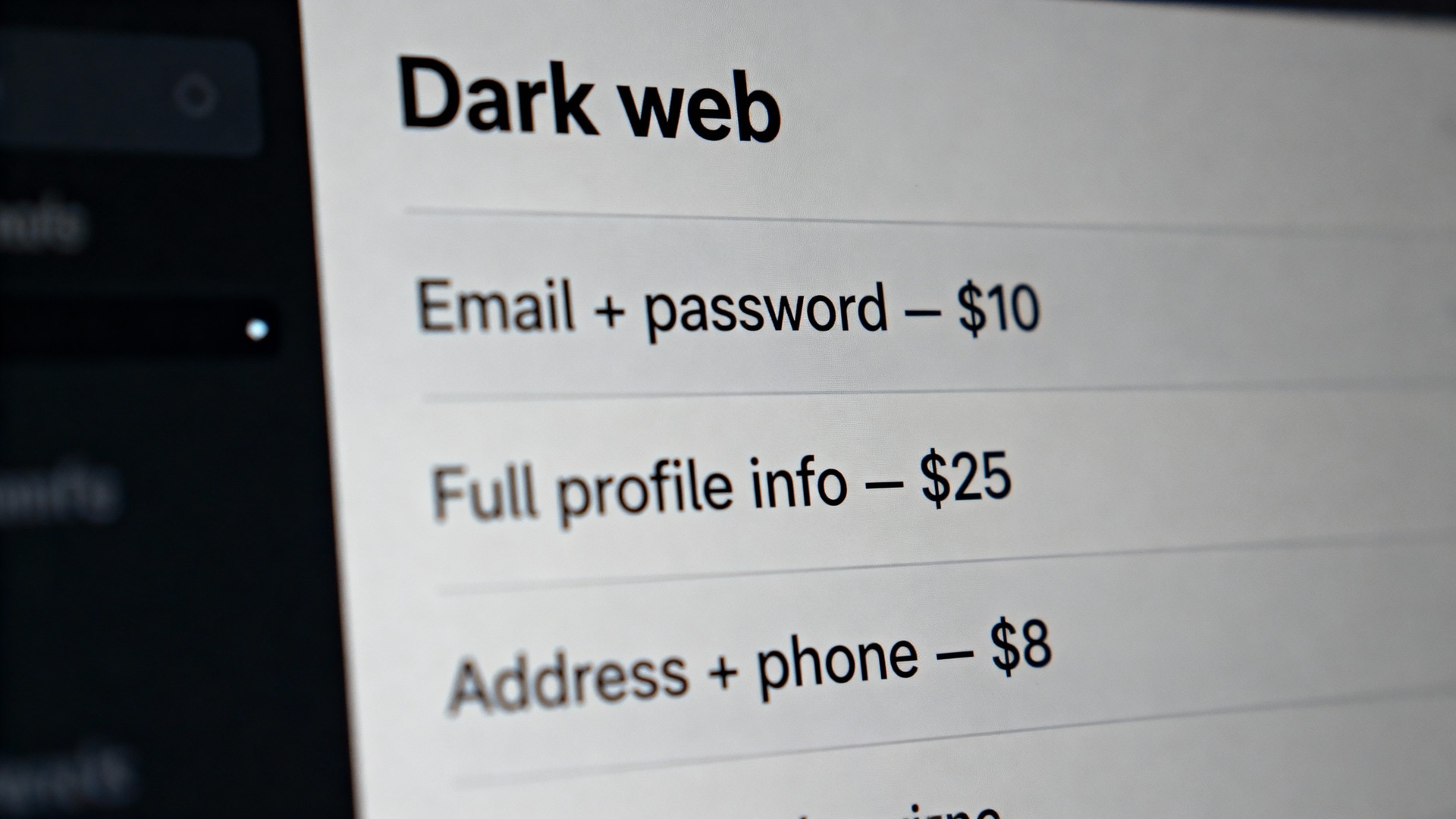
Here’s what your identity is worth today:
- Stolen credit card: $10–$50, depending on balance and freshness (Forbes).
- Social Security number: as little as $1–$2 (Experian).
- “Fullz” (complete identity kit: name, SSN, date of birth, address, bank details): $30–$1000, depending on detail level (Norton).
What this means for you: To hackers, you’re just another record in a bulk sale. To scammers, you’re a potential payday. Your “value” may be $2 online — but scammers can turn that into thousands if you fall for their trap.
The Triangle in Action
Here’s how the cycle works:
- Hackers steal or expose data (breach or leak).
- That data gets sold on the dark web.
- Scammers buy it and craft convincing, targeted attacks.
- The result? An endless cycle where one crime fuels another.
Scammers Turn Stolen Data Into Deception
This is where stolen information gets weaponized. Scammers transform anonymous data into convincing cons.
Instead of “Dear customer,” a phishing email greets you by name. Instead of guessing your bank, a caller already knows the last four digits of your card. Instead of a vague “It’s me, Grandma,” a scammer can say, “Grandma, it’s Kevin, I’m stuck in Denver,” because they bought those details.
Real example: In 2023, the FBI warned that criminals were combining leaked personal data with AI voice cloning. In one case, a grandmother wired $7,000 after hearing what she thought was her grandson’s voice — backed by real names and details from a data breach (FBI PSA).
What this means for you: The more details scammers have, the harder it becomes to doubt them. And most of those details come from hacks you never even heard about.

Why This Partnership Works
Hackers and scammers complement each other perfectly:
- Hackers scale. They can steal millions of records in a single night.
- Scammers personalize. They use that raw data to pressure individual victims.
- Together, they multiply harm. A breach that feels distant — “some company got hacked” — becomes intimate when a scammer calls you by name.
What this means for you: Don’t dismiss a breach in the news as “not my problem.” The real danger often comes later, when scammers use that data against you.
How Stolen Data Fuels the Triangle
When hackers steal data, it doesn’t stay theoretical. It travels through the dark web and lands in scammers’ hands — and that’s when it gets personal.
- $2 Social Security number → $15,000 loan. A scammer buys your SSN for pocket change (Experian) and applies for credit in your name.
- $10 email/password combo → account takeover. With your real login, criminals reset your bank password and lock you out.
- $50 credit card dump → shopping spree. Carding rings buy stolen cards and max them out on electronics within hours.
- $500 identity kit → a synthetic “you.” A complete package of SSN, address, and logins allows criminals to rent apartments, open accounts, or even commit crimes under your name (Forbes).
- $200 medical record → fake insurance claims. Fraudsters bill insurers for bogus treatments tied to your record.
- AI-voice “grandparent scams.” In 2023, the FBI warned about scammers combining leaked phone numbers with voice-cloning to impersonate loved ones.
Takeaway: for hackers and scammers, your details are raw material. For you, they can mean lost money, stolen identity, and a fight to reclaim your name.
How to Protect Yourself
You can’t stop hackers from breaking into companies, but you can reduce how much scammers can do with your data.
- Don’t reuse passwords. If one account falls, you don’t want the rest to follow.
- Turn on two-factor authentication. Even if your password leaks, scammers can’t log in without the extra code.
- Freeze your credit. This prevents criminals from opening loans in your name.
- Stay skeptical. If someone contacts you and “knows details,” remember: that info could come from a breach, not from legitimacy.
- Slow down. Scammers rely on panic and urgency. Taking a breath can save you thousands.
With Futureproof, you don’t have to track every threat online. We scan your info 24/7 and alert you the moment your data is at risk—so you can act fast and stay protected year-round.
Final Takeaway
Hackers and scammers may seem like separate threats, but they’re often partners in crime. Hackers steal in bulk. Scammers cash in one by one. Together, they form a cycle where your personal details — sometimes sold for just a dollar — are turned into fraud that costs victims billions.
For you, the defense is twofold: technical (strong passwords, two-factor authentication, credit freezes) and psychological (skepticism, slowing down, verifying before acting).
Because in the end, the scammer’s greatest weapon isn’t technology — it’s your trust.

At Futureproof, Kevin makes online safety feel human with clear steps, real examples, and zero fluff. He holds a degree in information technology and studies fraud trends to keep his tips up-to-date.
In his free time, Kevin plays with his cat, enjoys board-game nights, and hunts for New York’s best cinnamon rolls.